Although mdk3 is not (yet) included in BT4, it is a great tool to have.
(! with the release of Backtrack 4 Final, mdk3 is back with mdk3v6! Found in /pentest/wireless/mdk3/)
The below installation guide only applicable to Backtrack 4 Pre Final.
To get it installed, Virchanza wrote up a means to do so here;
http://forums.remote-exploit.org/backtrack-4-package-feature-requests/23803-mdk3.html
The contents of interest being ;
wget http://virjacode.com/projects/beefup/dloads/mdk3.tar.bz2
tar xjf mdk3.tar.bz2
cd mdk3-v5
sed -i 's|-Wall|-w|g' ./Makefile
sed -i 's|-Wextra||g' ./Makefile
sed -i 's|-Wall||g' ./osdep/common.mak
sed -i 's|-Wextra||g' ./osdep/common.mak
sed -i 's|-Werror|-w|g' ./osdep/common.mak
sed -i 's|-W||g' ./osdep/common.mak
make
make install
cd ..
rm mdk3.tar.bz2
rm -r mdk3-v5The reason I used it was to decloak hidden SSIDs by means of either a brute force or a dictionary attack, but there are many other interesting options with mdk3 !
In this test setup, I have an AP setup as follows ;
BSSID 00:13:D4:09:32:60 on Channel 3 Hidden SSID of 3 characters only.
So checking the test setup in airodump shows ;
In order to try to crack the hidden SSID, we can try a bruteforce attack, however it is always best to first try a dictionary to see if it isnt a standard essid name.
To get a decent dictionary list, you can get the one which the Church of WiFi used for their tables.
http://www.renderlab.net/projects/WPA-tables/
And of course you can drive around a bit and collect a few more to add.
The general usage in this case for using mdk3 with wordlist is ;
mdk3 [iface] p -c [channel] -t [bssid] -f [path to wordlist] -s [packets/sec]
So in my case;
mdk3 mon0 p -c 3 -t 00:13:D4:09:32:60 -f /wordlists/ssid.txt -s 50
(can do more packets per sec. but just for example's sake)
So when successful in finding the SSID and airodump is left running, the found SSID will pop up in airodump;
If the SSID cannot be found in the wordlist, then bruteforce approach can be tried, but only for short SSIDs.
It took my setup around 30min to crunch through all printable characters for the 3 character SSID..
The general usage of the bruteforce attack is as follows ;
mdk3 [iface] p -c [channel] -t [bssid] -b [character set] -s [packets/sec]
The brute force character set is as follows;
- a all printable
- l lower case
- u upper case
- n numbers
- c lower and upper case
- m lower and upper case plus numbers
It failed to correctly identify the essid on my test network when no limit was set (then it does max 300pps), however it did work succesfully when limiting to 150 pps.
Mind you it is being tested on a pretty old ASUS WL-530g router.. so not surprising really..
What works for other routers is probably simply a matter of trial and error.
Also, airodump seemed to conk out after about a minute of running possible ssids to the router with the message;
"Caught signal 14 (SIGALRM). Please contact the author!"
Anyway..
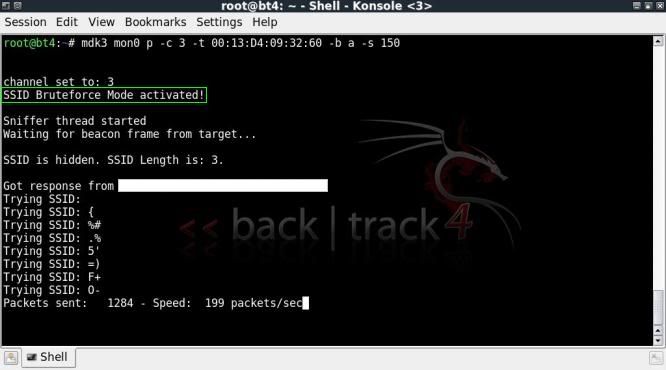
Starting up the attack using brute force;
mdk3 mon0 p -c 3 -t 00:13:D4:09:32:60 -b a -s 150
Again the results may vary using different packets/sec.
The screen will also show SSIDs of other networks which are picked up during the attack, but will then happily continue until either the full scope of the attack is finished, or the SSID is found.
MDK3 also has, among others, the interesting capability to effectively render communicating with a wireless network impossible, however to keep the posts semi short and sweet will come back to that another day..
MDK3 homepage - http://homepages.tu-darmstadt.de
A video showing the above ;
http://blip.tv/file/2681248
or
http://www.youtube.com/watch?v=52d1FsfJ2Ek




No comments:
Post a Comment